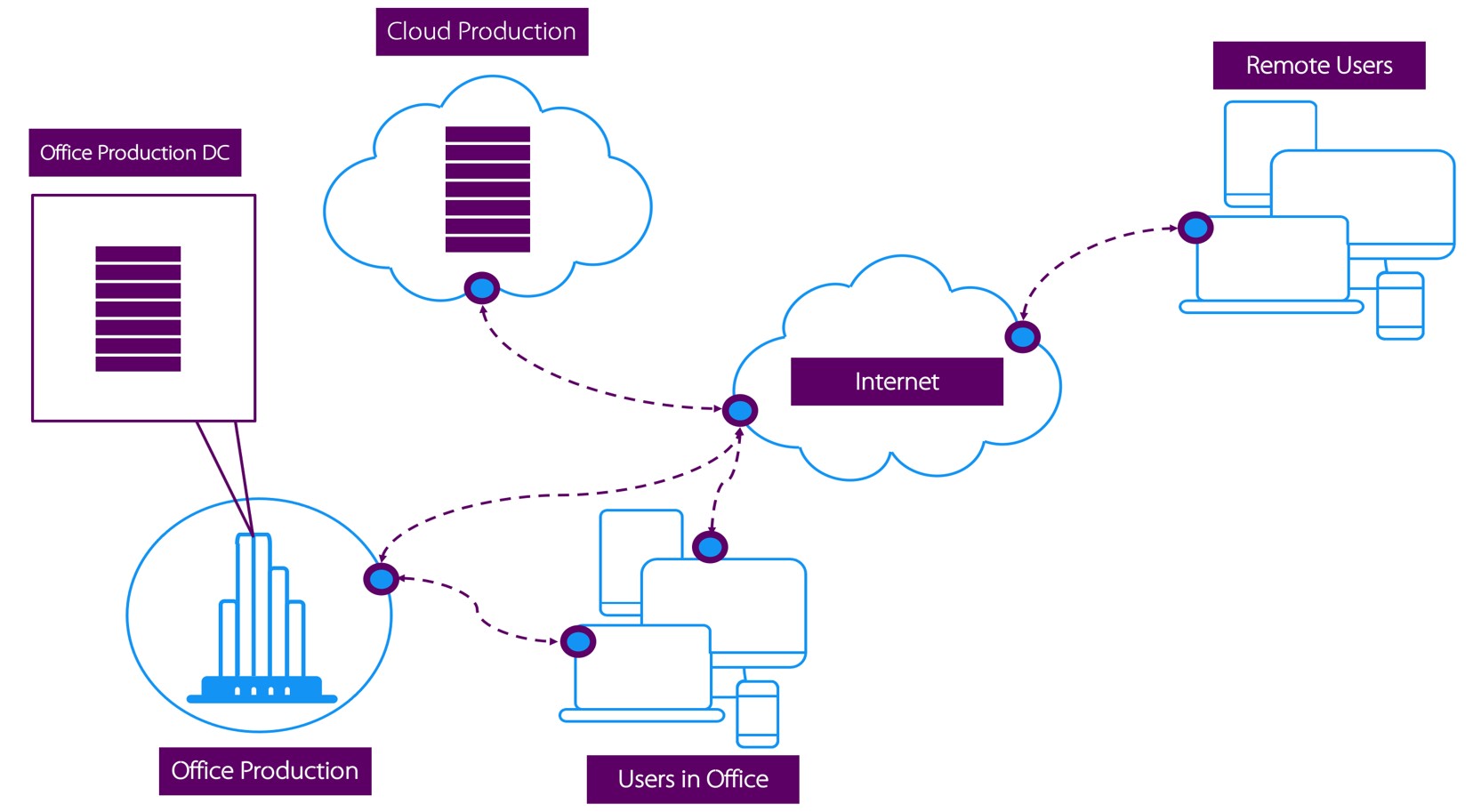
- Do you need remote access to desktop and web based applications as well as computers in the office on any device, without installations and configurations of problematic softwares?
- Or do you need access to office resources without making remote devices part of the corporate network, unlike VPN?
If your answer to the questions above is Yes, then the Software Defined Perimeter service by Trinspired Consult is what you’ve been searching for.